What Is SNMP? – A Comprehensive Guide
Park Place Professional Services
What is SNMP?
Table of contents
Why do you need SNMP? • How does SNMP work? • Basic commands of SNMP • Versions of SNMP
SNMP allows devices on a network to communicate, regardless of hardware and software. This provides network devices (routers, printers, servers, etc.) with a common language for sharing information with a network management system.
Why do you need SNMP?
The purpose of every network monitoring tool is to continually monitor and manage the health of network devices across an organization. Managing the health of network devices is necessary to ensure all applications and services employees and customers are using are working properly, which requires all physical hardware, network devices, and virtual network devices to work properly.
Dating back over 30 years, SNMP is the most ubiquitous way to monitor network devices today, bridging the connection into network devices that essentially allows a network professional to ask the question “How can I monitor you, device?” SNMP touches every single form of network monitoring you can imagine, but it’s actually quite simple in terms of functionality.
How does SNMP work?
What does SNMP do?
Every single network device can eventually experience problems, whether a router shuts itself off or a server goes down.
- For example: We’ve all got network routers that we connect to in our homes. If your router turns itself off, there’s no way to know unless you walk up to it to confirm there are no lights on. As an end user, you simply lose your internet connection, conclude that something has gone wrong, and pay a visit to your router.
Business networks include tens, hundreds, and sometimes thousands of network routers to monitor. Imagine the same scenario taking place in a sea of 10,000 routers. You’d need to know exactly which one to take a closer look at to determine where the actual issue lies.
For this reason, we have network monitoring platforms and ways to connect to those platforms to learn about the health of different network devices.
The simple network management protocol is a way to ask those devices what their health is at regular intervals. There’s lots of different questions you can ask, with the most basic being something like: “Are you okay?” every five minutes, for instance. Each time you ask that question, the network device would response back with “Yes,” “No,” – or it won’t respond at all if it’s completely lost power. In any of those cases, it becomes clear there’s an issue, giving the network professional taking care of the device an idea of its health status. “Are you okay?”, of course, is one of many questions you could ask. Think of SNMP as Siri for your network devices (or Google Assistant if you’re partial to Android) if you like.
- For example: If you’re monitoring a Windows laptop, you might decide to ask it another question, such as “What is your CPU percentage?” every five minutes, collecting and storing each value along the way (hypothetically, 52%, 63%, and 15%, respectively) as time series data which you can chart over a given period. You might also ask “What’s your memory allocation?”, or “Do you have any errors?” and again, store all those values in a series over time. Every device can be asked a myriad of different health questions, all of which are queried over SNMP.
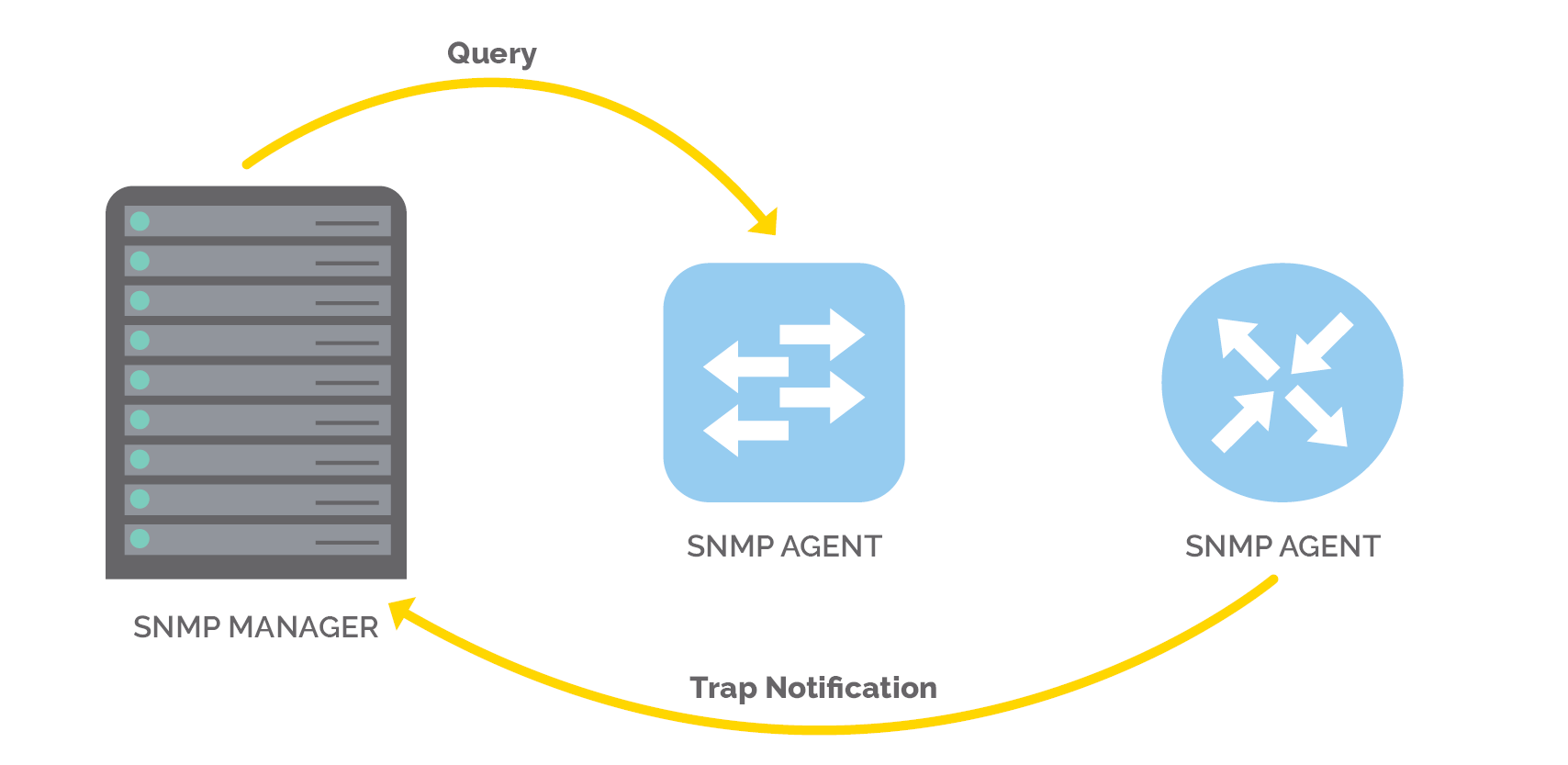
There are two ways SNMP works: polling or traps.
What is “SNMP polling”?
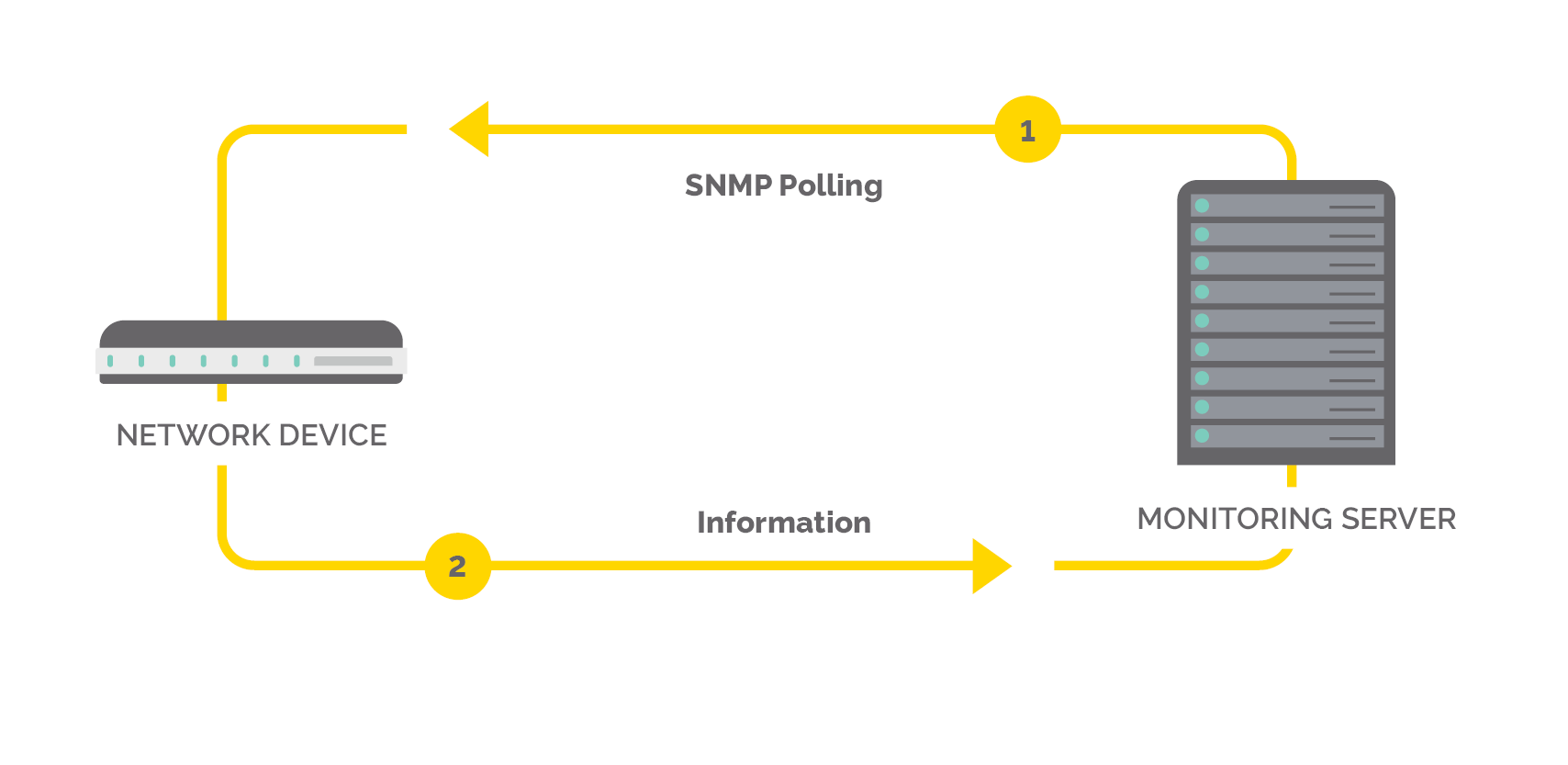
SNMP polling is simply network speak for the process described above: when you’re polling a network device for information and then the information is returned. Usually, SNMP polling occurs every five minutes automatically as part of your network management platform of choice. To do SNMP polling, a network device must have an SNMP agent installed on it.
Each piece of information returned from a poll is taken from a management information database, or MIB. Consequently, every network device with SNMP installed also has a MIB, which is a tiny database that lives on the devices. Most network devices have this software installed by default. The MIB is a list of all the different health metrics the device offers.
- For example: Consider a network router with a MIB that has hundreds of different pieces of information: CPU, memory, latency, disk queue length, name of the router, IP address of the router, location, etc.When the SNMP poller says “Tell me your name,” it goes out to the MIB which has the answer to the question and sends it back to the SNMP request. This can be displayed in a table, dashboard, or similar.
Each object within the MIB is classified by a MIB object identifier or OID, which are unique identifiers. When adding new devices to a network management system, often the most time-consuming part is parsing through MIBs, figuring out the type of data each OID represents, and selecting which ones you’re interested in in order to gain a full picture of the health of a given network device. You can’t poll a network device for every single OID number – not all of it will be useful for figuring out the health of the device in question. Therefore, part of the exercise in SNMP polling involves tailoring exactly what you query the device for.
What are “SNMP traps”?
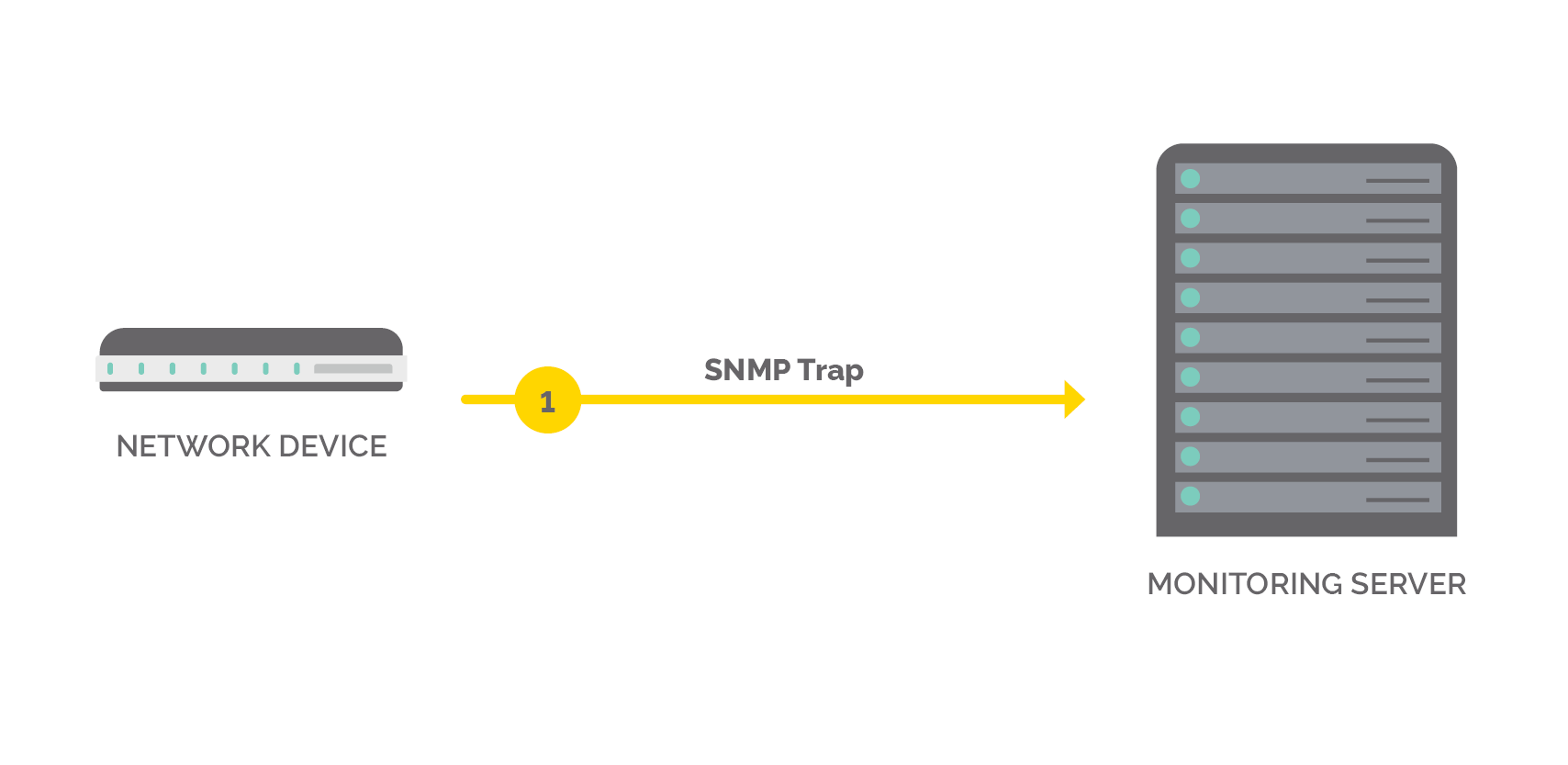
An SNMP trap is different than SNMP polling. Polling is proactive, requiring the effort of asking the network device for information and polling it back. Conversely, a trap is a push, not a pull. More specifically, every single network device can generate its own alerts and events if something goes wrong through a trap message.
- For example: Imagine a network device suddenly has a spike in CPU utilization that goes above 90%. Rather than waiting for you to poll it in five minutes to ask whether the CPU is high, it will send out an alert to say “My CPU is really high at the moment.”
Most network devices have SNMP traps. Traps must be sent somewhere, therefore you must configure your network management tool to receive them. Essentially, this is the exercise of declaring “If any of these specific events occur on network devices, point them at this network management tool so it can receive them and inform the network operator something’s gone wrong.”
The benefit of traps is that they’re more immediate, eliminating the potential for a critically important network device to go down for 4 minutes and 59 seconds before the next poll comes up to inform you something’s wrong. Instead, the network device will send alerts about the problem it’s having in real time.
What transport protocol does SNMP use?
SNMP uses user datagram protocol or UDP as its transport protocol. Since SNMP is a request/response protocol, the reliability of TCP isn’t required, as each request generates a response. If a response is not received, the SNMP application just reissues the request. Furthermore, there’s no need for sequencing because each request and response travels as a single datagram.
Basic commands of SNMP
Commands are the way in which you interrogate a network device to get information from it, initiated from the SNMP manager.
- For example(s): The most common command is the GET command, which is a normal question posed to a network device to say, “Get me this piece of information.” Another popular one is the GET BULK command, used when you’re retrieving a lot of different data from a network device using one single request. Traps are also technically commands, although initiated by agents as a signal to the SNMP manager.
The remaining commands are as follows:
- GET NEXT
- SET
- INFORM
- RESPONSE
Versions of SNMP
There are three main versions of the protocol: SNMPv1, SNMPv2c, and SNMPV3. The most widely used protocols are V1 and V2. V2 is the more secure adaptation of V1, commonly used for most network devices today. V3 is where you can expect to see most network monitoring and managing done in the future due to significantly enhanced security, however the transition will be slow.


